|
|
|
Illegitimate residential proxy services:
the case of 911.re and its IOCs
By Marc Frappier, Philippe-Antoine Plante, Guillaume Joly
{marc.frappier, plap1903, jolg2405} @usherbrooke.ca
Abstract
Residential proxy services (RPS) allow
someone to rent a residential IP address to use it as a relay for his/her
internet communications, providing anonymity and the advantage of being
perceived as a residential user surfing the web. For the visited servers,
the IP traffic appears to originate from the rented residential IP address, not
from the original RPS user. These RPS can be used in a legitimate manner
for several business purposes (e.g., market survey, seo, etc), allowing the RPS
user to bypass access control based on the IP source address (e.g., filtering
out VPN, cloud services, competitors, country-based access, etc).
However, they can also be used for hiding criminal activities and making it
very difficult to trace malicious traffic to its original source. Some
well-known RPS, like Brightdata, recruit residential proxies through some level
of informed consent, and filter/vet RPS clients to avoid illegitimate use. Other
RPS, like 911.re, recruit residential proxies with a less than clear consent
and do not filter at all RPS clients, opening the gate to an illegitimate use
of a residential proxy, exposing the person legally associated to the
residential proxy to some severe legal consequences. During the research we
identified two free VPN services that uses a subterfuge to lure users to
install software that looks legitimate but makes them part of the network.
These two software are currently unknown to most if not all antivirus
companies. This research enabled the discovery and exposure of the s911.re infrastructure
and over 120,000 residential nodes of its network.
Keywords
{RPAAS, Residential Proxies, s911.re,
malware, C2, command-and-control, C&C }
Timeline
January 2021 – Beginning of the research
project
November 2021- April 2022 – Active
collection phase
June 2022 – Presentation of the results
Introduction
Residential Proxies As A Service (RPAAS)
is a recent trend in internet anonymity services. It enables legitimate and
malicious actors to anonymise their network traffic by directing it through
residential nodes which behave like proxy servers, bypassing multiple security
mechanisms such has VPN detection. We assessed RPAAS providers and found the
911.re service. Beginning in January 2021, our research mainly focused on this
subscription-based service, openly available on the internet to any user.
911.re is known to be among the largest residential IP provider. It offers to
rent residential nodes without any vetting or verification process. We have
reverse engineered the infrastructure of the 911.re service and listed all
available residential nodes at the time of our capture.
At the time of this publication, the
binary and network signatures of its various recruiting programs are not
flagged as malicious traffic by antivirus systems. Residential node owners
listed on 911.re could face criminal or civil liability if their computer is
used by malicious actors, since the malicious traffic will appear to originate
from them. We have produced IOCs for residential proxy nodes and the 911.re
infrastructure. As of today, there are over 120 000 residential
proxy nodes in the 911.re network, distributed all over the world. Our research
identified two applications that recruit residential nodes to make them
available on the 911.re network.
Research methodology
Initially the team developed hypotheses on
the inner workings of the 911.re RPAAS based on known malicious botnet network
infrastructure knowledge. It was expected that the network would operate using
one or several command-and-control servers (henceforth called C2) to keep
persistent communications with recruited residential nodes. The main
challenges in operating such a network are to recruit nodes and to maintain
persistent communications with them to provide an adequate service level to
911.re users. Also, there must be nodes in several cities around the
world in order to make the service attractive to the 911.re users.
Initial hypotheses
·
The primary hypothesis was that there was some IOCs that could be collected by
sniffing the network link of a recruited node that we purchased through the
911.re service while generating a significative amount of network traffic in a
short lapse of time.
·
The proxy service is installed on the recruited residential node without
appropriate, informed consent of its owner.
·
The proxy system operates a botnet-like infrastructure.
·
The recruited node communicates multiple C2 that are located offshore or hosted
within a cloud server.
911.re service
The 911.re service is a paid subscription
service where end users can buy to rent residential nodes. The service appears
to have been operating since early 2018.
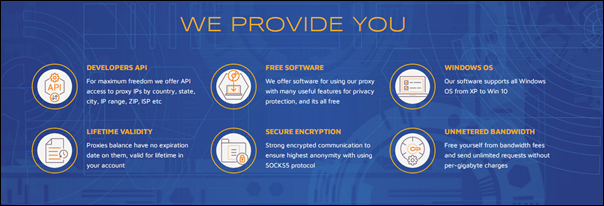
Image 1: 911.re website product features
The platform is operated in offshore
manner with the shell corporation International Media Ltd as owner of the service. There is currently no public
knowledge of the owners or operators of the 911.re service. Moreover, two
different shell corporations are used to sign the binaries in order to add
legitimacy to the software Mask VPN and Dew VPN. The end users do not
have full knowledge that they are part of the 911.re network when they install
Mask VPN or Dew VPN.
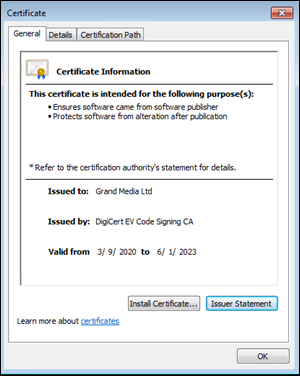
Image 2: Dew VPN binary certificate issued
to: Grand Media Ltd
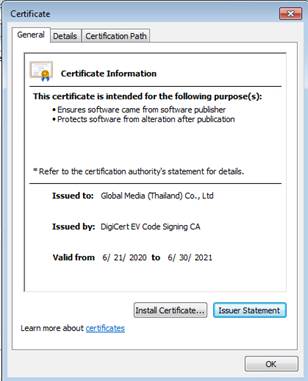
Image 3: Mask VPN binary certificate
issued to: Global Media Ltd
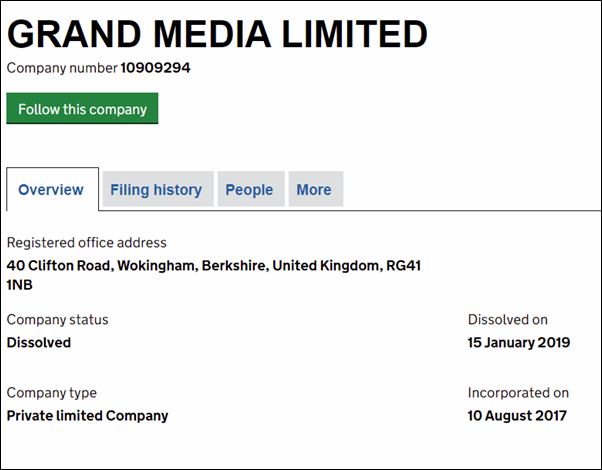
Image 4: Incorporation records for Grand
Media Limited (UK)

Image 5: Incorporation records for
International Media Limited (UK)
911.re Infrastructure
The 911.re infrastructure is designed to
obfuscate the true nature of the infection. The 911.re network modus operandi
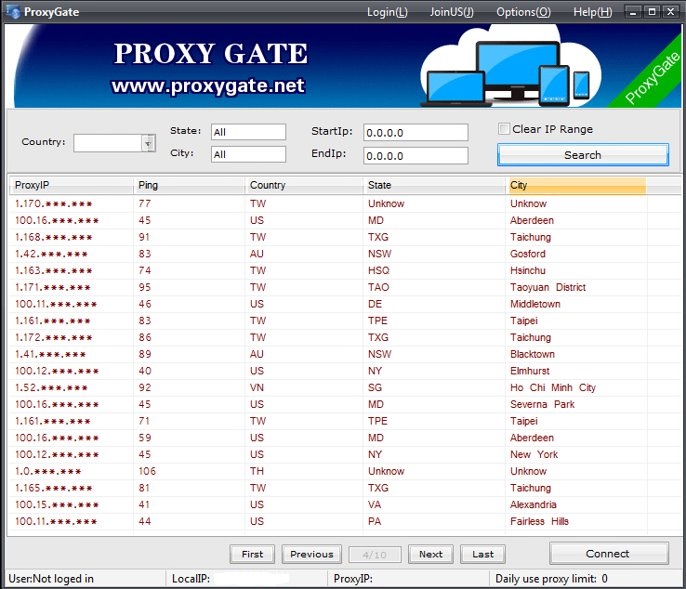
appears to date back in 2018, with the service Proxygate. The Proxygate
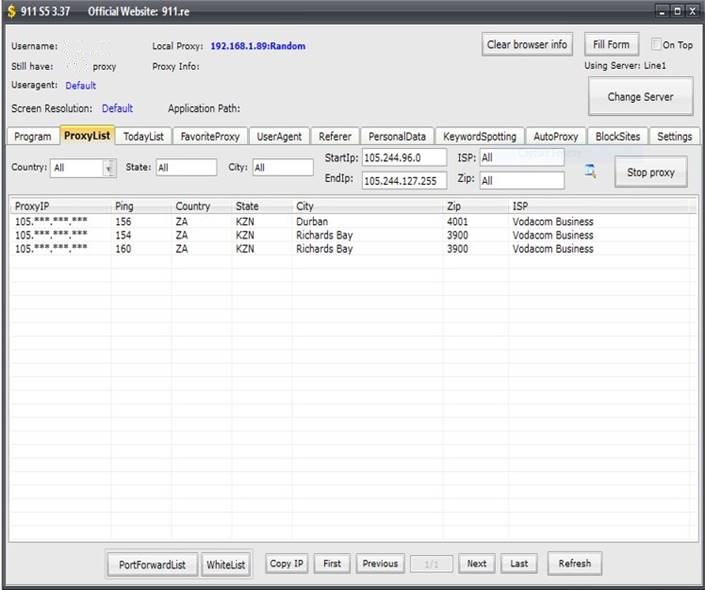
ancestor interface and the 911.re interface share several characteristics.
Participation in the network as a proxy
node for Proxygate was clearly stated and consensual, while it is less clear in
911.re. All the network traffic between the infected nodes and the
C2 server is encrypted. The infected nodes that have installed Mask VPN or Dew
VPN are still able to use the VPN software legitimately to navigate the
internet, however the service creates a backdoor and connects back to a C2
server located in the Krypt Technologies backend. This TCP connection in the
background also has a heartbeat and it is what makes the node available for
usage in the 911.re software.
|
Image 6: Proxygate inferface |
Image 7: 911.re interface |
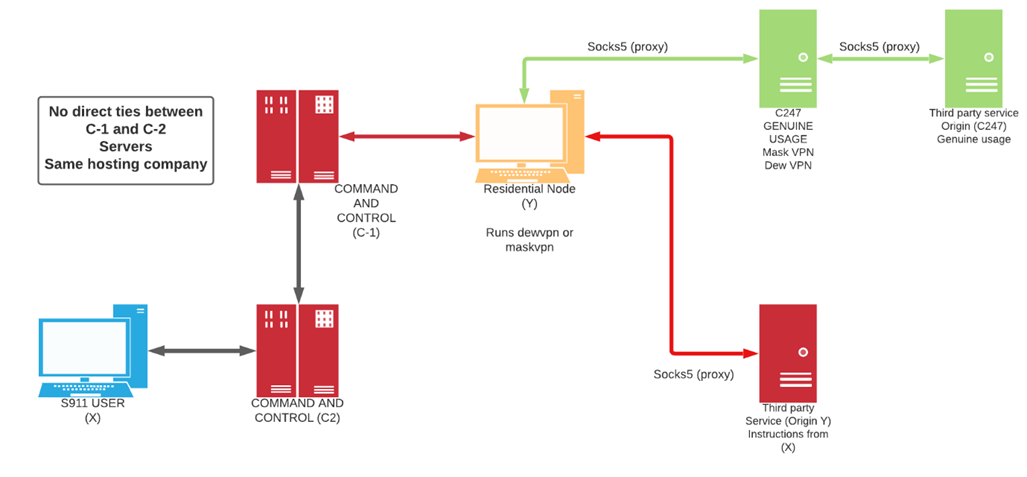
911.re does not operate in a simple
straight forward manner. The infrastructure is made so that it is complex to
reverse engineer. The infected nodes have either Mask VPN or Dew VPN installed.
They connect to a server that provides them with a legitimate free and
functional VPN service. The free VPN service provides the end user IPv4 within
the M247 ISP subnets. However, at the same time, their computer is joined to a
botnet like infrastructure, through a permanent TCP socket connection. This TCP
connection is made to the C2 servers of the 911.re backend infrastructure and
renders the node available for connections through the 911.re interface. A
heartbeat process is in place to ensure the node is listed as available. At no
time, there is direct connection between the infected node and the 911.re paid
subscriber even when the node is selected, and traffic passes through. All the
network traffic is always routed between the C2 servers that are USA based,
reducing the risk of anomaly detection by IDS or IPS systems. Mask VPN and Dew
VPN are using a custom implementation of the open-source OpenVPN.
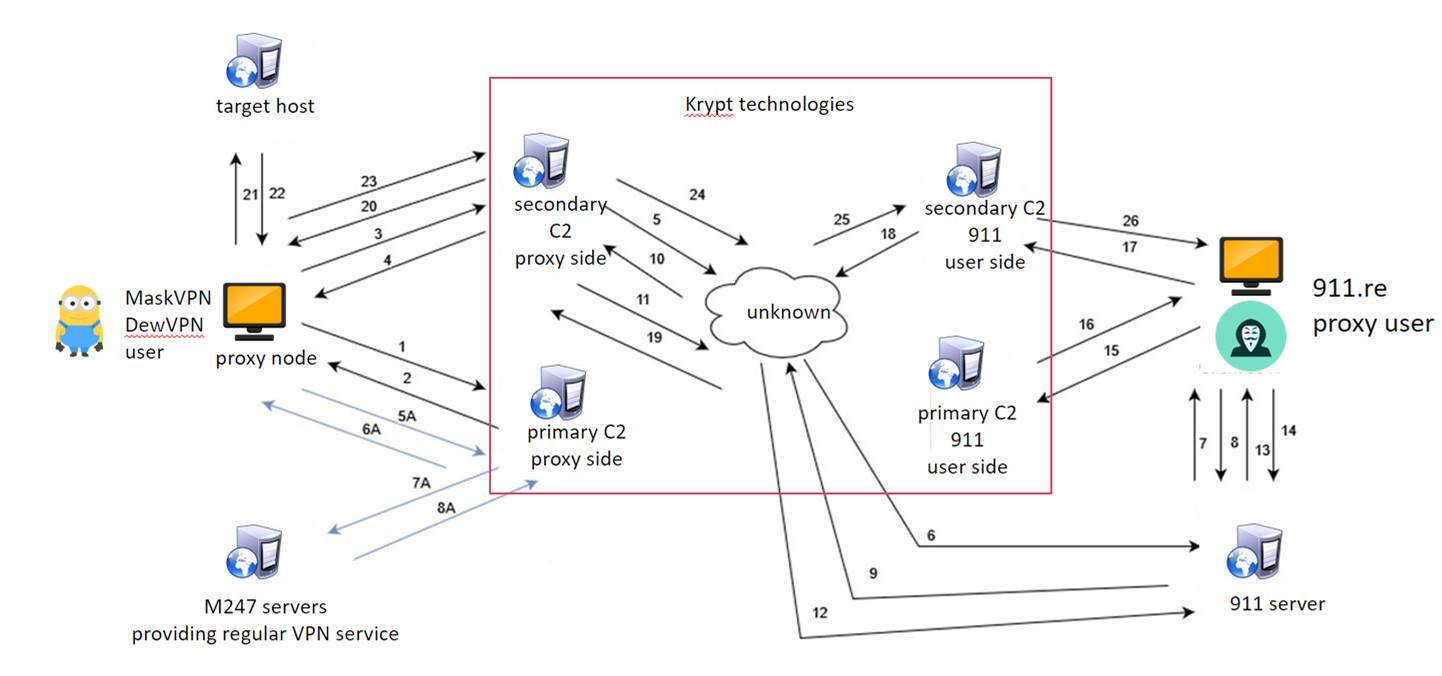
Methodology
With the collaboration of our research
partners, we were able to collect incoming and outgoing TCP traffic flow from
several infected nodes. This enabled us to discover a link between 911.re, and
one of its recruiting applications, Mask VPN. During our reverse analysis of
Mask VPN, we were able to identify another recruiting application, Dew VPN.
Deploying Mask VPN and Dew VPN on several
separate virtual machines in different OS / environments, we have analyzed the
behavior of the 911.re network. Installing Mask VPN or Dew VPN made the virtual
machine available for connections on the 911.re client application after about
15 minutes. Using the client application, we were successfully able to connect
and use the routable IPv4 address of the infected nodes with the 911.re client
with an active subscription. Additionally, there is currently no vetting process
for the end users, therefore enabling all sort of usage of the 911.re service.
A multi-thread collection infrastructure was created and used to collect around
120,000 nodes. The information collected on each node were the IPv4 and
the timestamp of the positive detection. Using Maxmind’s database we were able
to collect further information such has country, city, ASN and ISP or the
infected node IPv4.
911.re Network Extent
Our analysis enabled us to find a total of 118,804 nodes on the 911.re
network. The collection process began 2021-11-10 and ended on 2022-04-26. The
node collection process was made by using a specifically crafted multi-threaded
system. A full collection run normally lasts about 7 days.
Table 1: Total number of unique IPv4 occurrence
between 2021-11-10 and 2022-04-26
|
118,804 unique IPv4 nodes |
Table 2: Top 20 nodes occurrence per
Country
|
United States |
20022 |
|
South Korea |
12470 |
|
Peru |
9421 |
|
Japan |
9305 |
|
Canada |
8115 |
|
Spain |
7612 |
|
Taiwan |
7373 |
|
Italy |
4369 |
|
France |
4075 |
|
United Kingdom |
3776 |
|
Chile |
3504 |
|
Australia |
3140 |
|
Germany |
3123 |
|
Hong Kong |
2213 |
|
Belgium |
1759 |
Table 3: Top 10 Unique IPv4 occurrence per
ISP
|
Korea Telecom |
6556 |
|
Spectrum |
4343 |
|
Comcast Cable |
4291 |
|
Telefonica del Peru |
4246 |
|
Chungwa Telecom |
3141 |
|
Claro Peru |
2549 |
|
SK BroadBand |
2501 |
|
AT&T U-verse |
1745 |
|
Vodafone Germany Cable |
1570 |
|
NTT |
1562 |
During our analysis, nodes within several
major US-based Universities and Colleges, critical infrastructures such as
clean water, defence contractors, law enforcement and government networks were
seen as available for purchase with the 911.re interface.
911.re pricing

Proxy Node Vulnerabilities Exploitable by 911.re users
IP filtering-based service
Some ISP providers offer access to their
customer service (eg, Internet TV service, etc) without asking a user id and
password when the service request originates from one of their IP addresses,
because they assume that it is sufficient to authenticate the user based on the
source IP address. When the node is available as a residential proxy, the
911.re user can then access the ISP customer service as if he/she was the owner
of the residential proxy. Thus, an 911.re user can browse the account of
the residential proxy on its ISP provider and potentially gain confidential
information.
It would be interesting to investigate if
other web services allow one to bypass authentication based on the source IP
address of the request. This would also open the door to illegitimate use
of the residential proxy owner account by a 911.re user. Poorly designed
cookies could also be exploited.
Lateral movement attacks
The infection of a node enables the 911.re
user to access shared resources on the network such has local intranet portals
or other services. It also enables the end user to probe the LAN network of the
infected node.
DNS router cache poisoning
Using the internal router, it would be
possible to poison the DNS cache of the LAN router of the infected node,
enabling further attacks.
How to disable mask VPN and dew VPN
After conducting a full software
uninstall, usually the node becomes unavailable, and the persistent TCP
connection is no longer available. However, a full Operating System reinstall
is suggested.
1.
Completely uninstall either or both
software through the Windows Programs and Features from the Control Panel;
2. Net stop MaskVNService
3. Net stop DewVPNService
4. SC DELETE MaskVNService
5. SC DELETE DewVPNService
Conclusion
This research enabled the discovery of a
mid scale botnet-like infrastructure where the payload is unknown to antivirus
compagnies and that operates in several networks, such as corporate, government
and critical infrastructure. The 911.re network uses at least two free VPN
services to lure its users to install a malware-like software that archives
persistence on the user’s computer. The full extent of the scale of the network
is currently unknown and is of interest for further research.
Indicators of compromise (IOCs)
X509 Certificates
Name Global Media (Thailand) Co., Ltd
Issuer DigiCert EV Code Signing CA
Valid From 2020-06-22 00:00:00
Valid To 2021-06-30 12:00:00
Algorithm sha1RSA
Thumbprint
BA2CC98AE9760F4B584973A51436D6896BA20291
Serial Number 0C 27 3D 79 82 0C D6 0B 57
09 19 4D 6E 42 B0 16
Name Grand Media Ltd
Issuer DigiCert EV Code Signing CA
Valid From 2020-03-10 00:00:00
Valid To 2023-06-01 12:00:00
Algorithm sha1RSA
Thumbprint
DF58A6BE47E831DE8D7A36944CFC8C456F1E4E3E
Serial Number 09 62 7F B7 13 23 16 85 DC
FD 5A 5C 20 AA A8 08
Binaries
·
Maskvpn.exe (2/68 virus total)
MD5: a220528f31dceddc955b791b13ac4989
SHA-1: 57a83b83a11b6e27c9e88a7835d8a84744d79bdd
SHA-256:
e801fa187027537337d8b4e4bde3a7da95499172f6b1477830a216d0a385518b
·
Dewvpn.exe (1/67 virus total)
MD5: 12059484a8951a8356c60c46f659a35e
SHA1: 3916aeaa61a6e97d6c1746b18c05fd77584de5d8
SHA256: daa21c58a1ace38d1eebcda6fef3502fa3492ccf09fbccfa6ce103c9222d9afc
·
maskvpn-setup.exe (2/68 virus total)
MD5: f9634d85ca0138cfddfe6e58fa1c6160
SHA1: 5ffa0b96b7257d804beddb87b0a21e871a1296b4
SHA256:
1013eb0e3dbbc16c8b6d0659cca46a084e767b2d9bb8e498e07016bfdb978780
·
mask_svc.exe (1/67 virus total)
MD5: c6b1934d3e588271f27a38bfeed42abb
SHA1:08072ecb9042e6f7383d118c78d45b42a418864f
SHA256: 35ec7f4d10493f28d582440719e6f622d9a2a102e40a0bc7c4924a3635a7f5a8
·
DewVPN-Setup.exe (1/67 virus total)
MD5: 8e8b072c93246808a7f24554ca593c59
SHA1: d06418cacd11e25af37a41724d55dffc24d6fe5b
SHA256: f422a38d72785c402948c94ae81336383a9fd48167272f29cdc434ce7e51e02b
·
dew_svc.exe (0/69 virus total)
MD5: 5feb35a7186a5be50b7aa158866b8aa3
SHA1:c0c7e272f3e48d8dfe559aa5f63ad3a46c76fb9e
SHA256: a8e72d202f9a83e6bdfd03a822fae6d4ee2d4b35a6f73a06e9d59e2e49b3070a
DNS
queries:
·
vpn[.]maskvpn[.]org
·
user[.]maskvpn[.]org
·
net[.]dewvpn[.]com
·
wan[.]dewvpn[.]net
·
connect[.]dewvpn[.]cc
IPv4:
·
98.126.176.51
·
98.126.176.52
·
98.126.176.53
======
·
67.198.169.2
·
98.126.244.26
·
98.126.13.146
·
174.139.80.66
·
67.229.60.114
·
174.139.78.106
·
98.126.1.130
·
174.139.100.202
·
67.198.134.186
· 98.126.5.106
Outgoing
TCP ports used by Mask VPN and Dew VPN to initiate persistent C2 communications
·
441 TCP
·
430 TCP
·
433 TCP
·
434 TCP
·
436 TCP
·
440 TCP
·
439 TCP
·
435 TCP
·
428 TCP
·
432 TCP
·
438 TCP
References:
X. Mi et al., "Resident Evil: Understanding Residential IP Proxy as
a Dark Service," 2019 IEEE Symposium on Security and Privacy (SP),
2019, pp. 1185-1201, doi: 10.1109/SP.2019.00011.